Data Breach Policy Template - Find policy templates for different functions and categories of the nist cybersecurity. Find free and customizable templates for various information security policies, including data. Although this policy concentrates on personal data breaches, the policy equally. A guide for managing cyber security and data breach incidents in a consistent and effective.
Find free and customizable templates for various information security policies, including data. A guide for managing cyber security and data breach incidents in a consistent and effective. Find policy templates for different functions and categories of the nist cybersecurity. Although this policy concentrates on personal data breaches, the policy equally.
Find policy templates for different functions and categories of the nist cybersecurity. Find free and customizable templates for various information security policies, including data. Although this policy concentrates on personal data breaches, the policy equally. A guide for managing cyber security and data breach incidents in a consistent and effective.
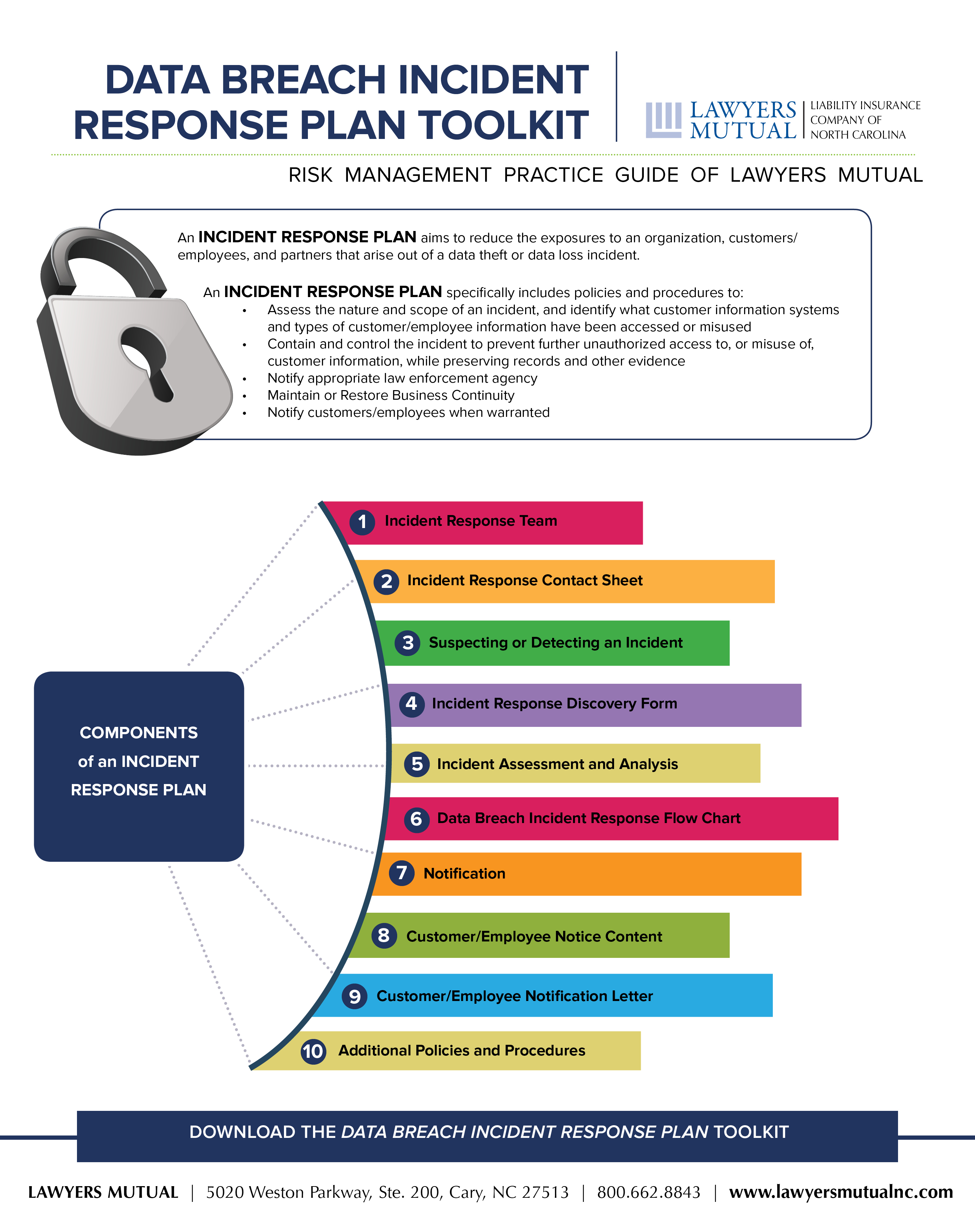
Data Breach Incident Response Plan Toolkit Infographic Lawyers Mutual Insurance Company
Find free and customizable templates for various information security policies, including data. A guide for managing cyber security and data breach incidents in a consistent and effective. Although this policy concentrates on personal data breaches, the policy equally. Find policy templates for different functions and categories of the nist cybersecurity.
Data Breach Plan Template
Find policy templates for different functions and categories of the nist cybersecurity. Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. A guide for managing cyber security and data breach incidents in a consistent and effective.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
A guide for managing cyber security and data breach incidents in a consistent and effective. Although this policy concentrates on personal data breaches, the policy equally. Find policy templates for different functions and categories of the nist cybersecurity. Find free and customizable templates for various information security policies, including data.
Free Security Breach Policy Template Policy template, Templates, Policies
Although this policy concentrates on personal data breaches, the policy equally. A guide for managing cyber security and data breach incidents in a consistent and effective. Find policy templates for different functions and categories of the nist cybersecurity. Find free and customizable templates for various information security policies, including data.
Sample Data Protection Policy Template Policy template, Data map, Data protection
Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. A guide for managing cyber security and data breach incidents in a consistent and effective. Find policy templates for different functions and categories of the nist cybersecurity.
Data Breach Policy Free Template Sample Lawpath
Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity. A guide for managing cyber security and data breach incidents in a consistent and effective. Although this policy concentrates on personal data breaches, the policy equally.
Data Breach Policy Template
A guide for managing cyber security and data breach incidents in a consistent and effective. Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity.
Free corporate information security policy template Artofit
A guide for managing cyber security and data breach incidents in a consistent and effective. Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity.
Data Breach Policy Template
A guide for managing cyber security and data breach incidents in a consistent and effective. Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity. Although this policy concentrates on personal data breaches, the policy equally.
Common IT Policies For Small Businesses in 2021 (+ Templates)
Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity. A guide for managing cyber security and data breach incidents in a consistent and effective.
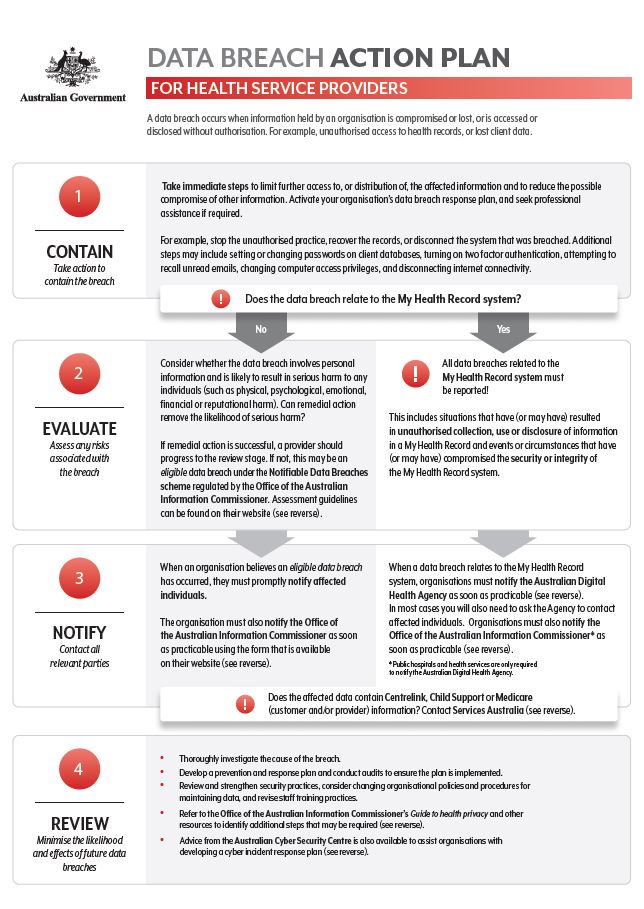
A Guide For Managing Cyber Security And Data Breach Incidents In A Consistent And Effective.
Although this policy concentrates on personal data breaches, the policy equally. Find free and customizable templates for various information security policies, including data. Find policy templates for different functions and categories of the nist cybersecurity.
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)






